- I've been working on setting up a Meraki MX100 firewall and migrating our client VPN from AnyConnect to the client VPN from Meraki. This means we have to use the built-in Windows VPN client which I've got working in a full-tunnel connection. I also worked through the Windows CMAK setup to get a connection profile we can distribute.
- I have a static ip on the ASA5510, but no staic ip on the Meraki MX. We only use dhcp from all our ASA5510 on the outside. We will not buy a static ip to all our ASA5505. So is it possible to create a VPN tunnle to ASA5510(Static ip-outside) from a Meraki MX65W(dhcp-outside)?
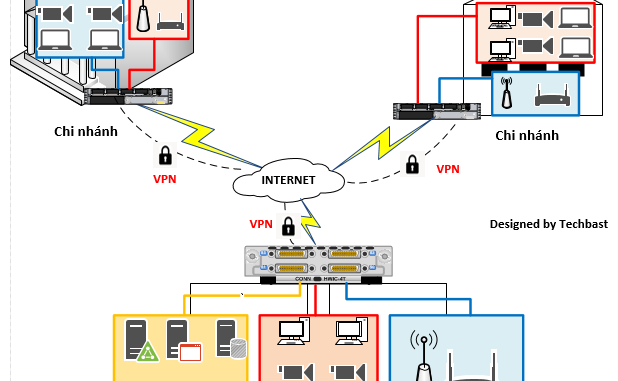
We have Meraki MR30H access points in several remote locations for our employees. At the main office, there is an MX-100 acting as a VPN concentrator for those MR30H APs. The MR30H APs tunnel back to two VLANs on that MX-100. AnyConnect Specific Features. AnyConnect is more than just a VPN client. It is a fully-fledged end-point mobility client solution. However, unlike the AnyConnect implementation on the ASA or FirePOWER with support for multiple features like Host scan, Web launch, etc, the MX security appliance supports SSL Core VPN and other AnyConnect modules that do not require additional configuration on. Meraki Community Solved: to configure SmartSecurity Anyconnect to Meraki. Avoid LAN overlap. DNS utilize technology to spur a AnyConnect connection MX - Cisco Community using DHCP- Forward for user VPN connections.
AnyConnect supports authentication with either RADIUS, Active Directory, or Meraki Cloud. For more details on AnyConnect configuration, refer to the AnyConnect configuration guide.

Note: Systems Manager with Sentry is not supported with AnyConnect.
Note: SAML authentication is not supported at this time.
Meraki Cloud Authentication
Note: IPsec must be enabled and users must be authorized on the IPsec settings tab.
Use this option if an Active Directory or RADIUS server is not available, or if VPN users should be managed via the Meraki Cloud. To add or remove users, use the User Management section at the bottom of the page. Add a user by clicking 'Add new user' and entering the following information:

Name: Enter the user's name.
Email: Enter the user's email address.
Password: Enter a password for the user or click 'Generate' to automatically generate a password.
Authorized: Select whether this user is authorized to use the client VPN.
To edit an existing user, click on the user under the User Management section. To delete a user, click the X next to the user on the right side of the user list.
When using Meraki-hosted authentication, the user's email address is the username that is used for authentication.
RADIUS
Use this option to authenticate users on a RADIUS server. Click Add a RADIUS server to configure the server(s) to use. Enter in the IP address of the RADIUS server, the port to be used for RADIUS communication, and the shared secret for the RADIUS server.
Note: Only one RADIUS server is supported for authentication with AnyConnect today.
Add MX security appliance as RADIUS clients on the NPS server.
In order for the MX to act as an authenticator for RADIUS, it must be added as a client on NPS.
Open the NPS server console by going to Start > Programs > Administrative Tools > Network Policy Server.
You’ll take the following steps each time you connect to your PS4 console from your Windows PC. Turn on your PS4 console or put it into rest mode. Use a USB cable to connect your controller to your Windows PC. You can also use a DUALSHOCK®4 USB wireless adaptor. Launch PS Remote Play on your Windows PC, and then select Sign In to PSN. Pair DUALSHOCK®4 wireless controller with PC or Mac. If you would like to use your DUALSHOCK 4 wireless controller with compatible games and applications on a PC or Mac, you can connect via Bluetooth or a compatible micro USB cable.
 With Remote Play, you can control your PlayStation® console remotely wherever you have a high-speed internet connection. Using the PS Remote Play app, you can control your PlayStation®5 console or PlayStation®4 console from a device in a different location. For example, you can use a computer in another room or a smartphone. when you’re out to enjoy PS5™ and PS4™ games.
With Remote Play, you can control your PlayStation® console remotely wherever you have a high-speed internet connection. Using the PS Remote Play app, you can control your PlayStation®5 console or PlayStation®4 console from a device in a different location. For example, you can use a computer in another room or a smartphone. when you’re out to enjoy PS5™ and PS4™ games.In the left-side pane, expand the RADIUS Clients and Servers option.
Right-click the RADIUS Clients option and select New.
Enter a Friendly Name for the MX security appliance or Z teleworker gateway RADIUS client.
Enter the IP address of your MX security appliance or Z teleworker gateway. This IP will differ depending on where the RADIUS server is located:
On a local subnet: use the IP address of the MX/Z on the subnet shared with the RADIUS server
Over a static route: use the IP address of the MX/Z on the subnet shared with the next hop
Over VPN: use the IP address of the MX/Z on the highest-numbered VLAN in VPN
Create and enter a RADIUS Shared Secret (make note of this secret, you will need to add this to the dashboard).
Note: Currently only ASCII characters are supported for RADIUS shared secrets, unicode characters will not work correctly.
Press OK when finished.
Collaborate for free with online versions of Microsoft Word, PowerPoint, Excel, and OneNote. Save documents, spreadsheets, and presentations online, in OneDrive. Share them with others and work together at the same time. The Microsoft 365 Enterprise and Office 365 Enterprise plans (including standalone plans such as Exchange Online) and Microsoft 365 Apps for enterprise are available for annual commitment payment. Annual commitment payment: You sign up for a one-year subscription, but you can choose to pay month to month or pay for the entire year at the time you sign up. Microsoft office 365 business essentials. Microsoft 365 Business Basic, $5.00 user/month (annual commitment) Buy now. Or buy for $6.00 per user/month with a monthly commitment. Try free for 1 month 4. Best for businesses that need easy remote solutions, with Microsoft Teams, secure cloud storage,. There are several Microsoft 365 for business plans that you or your organization can choose from when you sign up for one of Microsoft's cloud services. After your organization signs up for Microsoft 365, the admin can assign different Microsoft 365 licenses to each user account. Office 365 Business is now Microsoft 365 Apps for business Why did you change the name from Office 365 to Microsoft 365? We changed the name to be more reflective of the range of features and benefits in the subscription.
For additional information or troubleshooting assistance, please refer to Microsoft documentation on RADIUS clients.
Configure a RADIUS Connection Request
In the NPS server console, navigate to Policies > Connection Request Policies. Right-click the Connection Request Policies folder and select New.
In the Connection Request Policy Wizard, enter a policy name and select the network access server type unspecified, then press Next.
Click Add to add conditions to your policy. Access-request messages will need to meet these conditions to be allowed access.
From the list of conditions, select the option for NAS-Port-Type. Select VPN Virtual and press Next
Press Next on the next three pages of the wizard to leave the default settings intact.
Review the settings, then press Finish.
Configure a RADIUS Network Policy.
In the left-side pane of the NPS server console, right-click theNetwork Policies option and select New.
In the Network Policy Wizard enter a policy name and select the network access server type unspecified, then press Next.
Click Add to add conditions to your policy.
From the list of conditions, select the option for Windows Groups. Click Add Groups and enter the name you would like to give client VPN permission to.
From the list of conditions, select the option for NAS-Port-Type. Select VPN Virtual and press Next.
Leave the default settings on the Specify Access Permission page and press Next.
Deselect all checkboxes and select Unencrypted authentication (PAP, SPAP). An informational box will be displayed, press No to continue, and press Next. Refer to this doc for security information about using PAP.
Press Next on the next two pages of the wizard to leave the default settings intact.
Description Heed Adventure Bay's call for help in PAW Patrol: On a Roll! For the Nintendo Switch. Ryder and all eight PAW Patrol pups with unique abilities take on 16 rescue missions in eight different locations for fun-filled community action. Paw patrol switch. PAW Patrol is on a roll! No job is too big, no pup is too small! The PAW Patrol is ready to save the day in Adventure Bay on 16 exciting rescue missions, but they can only do it with your help! My daughter loves PAW patrol she is only 16 months old so thought I would get her this, not for her to Play as such for us me and my partner to play with her to help her learn as she likes to touch our xbox controllers and our switch lites, must say it's not a bad games either for a 31 year old to play.
Review the settings, then press Finish.
Meraki Mx Vpn Anyconnect
Active Directory
Use this option if user authentication should be done with Active Directory domain credentials. You will need to provide the following information:
Short domain: The short name of the Active Directory domain.
Server IP: The IP address of an Active Directory server on the MX LAN.
Domain admin: The domain administrator account the MX should use to query the server.
Password: Password for the domain administrator account.
For example, considering the following scenario: Users in the domain test.company.com should be authenticated using an Active Directory server with IP 172.16.1.10. Users normally log in to the domain using the format 'test/username' and you have created a domain administrator account with username 'vpnadmin' and password 'vpnpassword'.
The Short domain would be 'test'
The Server IP would be 172.16.1.10.
The Domain admin would be 'vpnadmin'
The Password would be 'vpnpassword'
Note: Only one AD server can be specified for authentication with AnyConnect at the moment. The MX does not support mapping group policies via Active Directory for users connecting through the client VPN. Refer to this document for more information on integrating with client VPN.
Certificate-based authentication
The AnyConnect server on the MX supports client certificate authentication as a factor of authentication. If certificate authentication is enabled, the AnyConnect server will use the uploaded trusted CA certificate to validate authenticating clients before requesting for the users' credentials. AnyConnect on the MX does not support certificate-only authentication at this time. Authenticating users must input credentials once certificate authentication succeeds. If certificate authentication fails, the AnyConnect client will report certificate validation failure.
Meraki Vpn Certificate
Multi-Factor Authentication with RADIUS or Active Directory as a Proxy
MFA is not natively supported on the MX, however, you can configure MFA with your RADIUS or Active Directory server. The MFA challenge takes place between the RADIUS/Active Directory/Idp and the user. The MX will not pass any OTP or PINs between the user and RADIUS. The user connects to the MX and gets prompted for username and password, the MX passes credentials to the RADIUS or AD server, then the RADIUS or AD server challenges the user directly (not through the MX). The user responds to RADIUS or AD server, possibly via push notification, etc, then the RADIUS or AD server tells the MX that the user has successfully authenticated. Only then is the user allowed access to the network. Refer to this document for more information on authentication.
Meraki Vpn Device
RADIUS Time-Out
Meraki Vpn Anyconnect Free
The default RADIUS time-out is three seconds. This is how long the AnyConnect server will wait for a response from the RADIUS sever before failing over to a different RADIUS server or ignoring the response entirely. To support two-factor authentication, you can increase the RADIUS time-out by modifying the RADIUS time-out field on the AnyConnect Settings page. The configurable time-out range is 1 - 300 seconds.
